As part of our efforts to better our community, both online and offline, we built a new tool for examining the differences between two .phar files. We call it Pharaoh, and we just released its code on Github under the MIT License.
Why Would Anyone Need Pharaoh?
Let's say the maintainers of a popular PHP project distributes their deliverable in a .phar file (PHP Archive). Furthermore, let's assume their download server (or one of their mirrors) gets hacked. The attackers succeed in replacing the .phar with an identical copy, save for a few extra lines of malicious code in the stub (the part that gets executed when you run a .phar from command line).
Pharaoh allows users to detect malicious tampering. All you have to do is follow these steps:
- Obtain the source code for the project. Check out the appropriate release tag, if need be.
- Obtain the sketchy .phar from the project website. Save it as foobar-untrusted.phar.
- Build a new .phar from the source code. Call it foobar-from-source.phar.
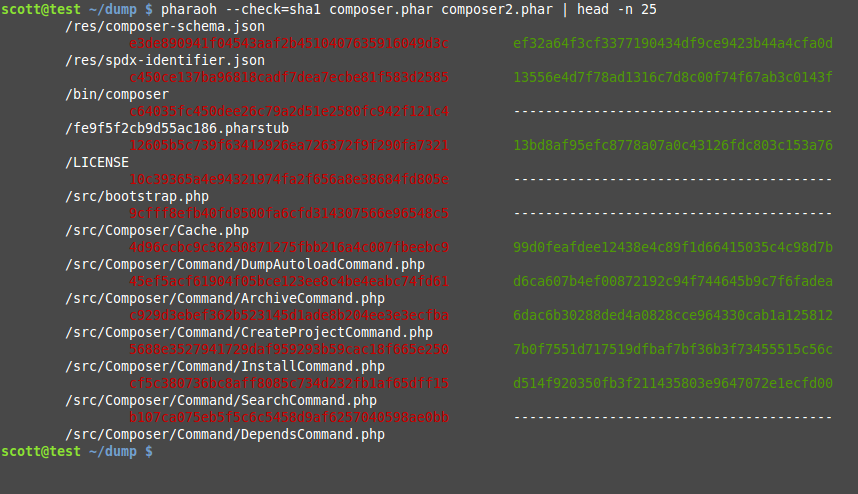
- Run
pharaoh foobar-from-source.phar foobar-untrusted.phar
If you make it to step 4 and have worked with Git and PHP before, you should be able to quickly decide if the .phar you downloaded is legitimate or not.
We will be using Pharaoh to verify that .phar files can be built deterministically from their source code, and to ensure the copy we sign in the distributed ledger for ASGard contains no nasty surprises. We also imagine tools like Pharaoh could be instrumental for detecting targeted malware attacks against software developers in the wild as part of a threat intelligence framework.