

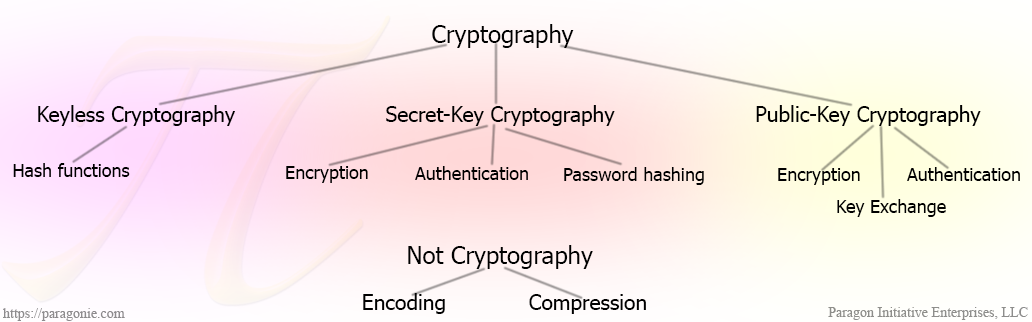
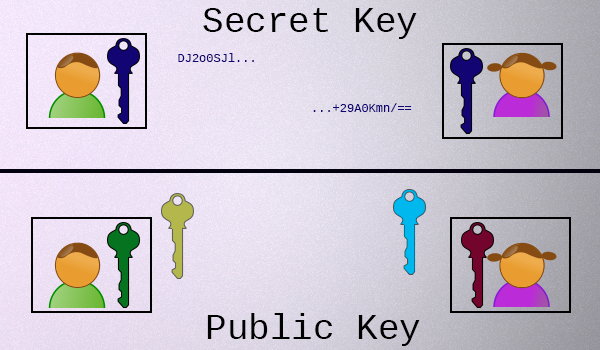
 Here's all you need to know right now: Unlike secret key encryption, which involves a single secret key that is held by both parties, in public key cryptography, each participant has **two keys**:
* Each participant has a **private key**, which they never share.
* Each participant also has a **public key**, which is mathematically related to their private key, which they share with everyone.
It is unfortunate that the "key" terminology from secret key cryptography stuck when public key cryptography was discovered, as there aren't very many physical systems that are intuitively similar to what's going on here. Some people have attempted to [explain public key cryptography using colors](https://www.youtube.com/watch?v=3QnD2c4Xovk) or [detailed explanations](http://crypto.stackexchange.com/q/292/24405). If you're interested in the intimate details, we recommend both of the links in the previous sentence.
For everyone else, if you can accept these premises, understanding the rest isn't hard:
* To use public key cryptography, you generate a key-pair and share the public key, but keep the private key to yourself. (In most cases, every participant does this.)
* There is only one private key for any given public key.
* Both of the keys in a given key-pair are related to each other, mathematically.
* Given a public key, it is almost impossible to figure out what the private key is.
* Given a private key, you can near-instantly calculate the related public key.
Got it? Let's build something with this understanding.
Here's all you need to know right now: Unlike secret key encryption, which involves a single secret key that is held by both parties, in public key cryptography, each participant has **two keys**:
* Each participant has a **private key**, which they never share.
* Each participant also has a **public key**, which is mathematically related to their private key, which they share with everyone.
It is unfortunate that the "key" terminology from secret key cryptography stuck when public key cryptography was discovered, as there aren't very many physical systems that are intuitively similar to what's going on here. Some people have attempted to [explain public key cryptography using colors](https://www.youtube.com/watch?v=3QnD2c4Xovk) or [detailed explanations](http://crypto.stackexchange.com/q/292/24405). If you're interested in the intimate details, we recommend both of the links in the previous sentence.
For everyone else, if you can accept these premises, understanding the rest isn't hard:
* To use public key cryptography, you generate a key-pair and share the public key, but keep the private key to yourself. (In most cases, every participant does this.)
* There is only one private key for any given public key.
* Both of the keys in a given key-pair are related to each other, mathematically.
* Given a public key, it is almost impossible to figure out what the private key is.
* Given a private key, you can near-instantly calculate the related public key.
Got it? Let's build something with this understanding.
| Cryptographic Hashes | Password Hashes |
|---|---|
|
|
A lot of developers will either encode or compress information and assume their solution provides the same level of security as actual cryptographic features simply because the output is not human readable. It doesn't. Encoding and compression algorithms are both **reversible, keyless transformations of information**. Encoding specifies how information should be represented in human-readable text. Compression attempts to reduce an input to as little space as possible. Both are useful, but they are not cryptographic features.
This may very well be the worst password storage function ever written.